Study Guide
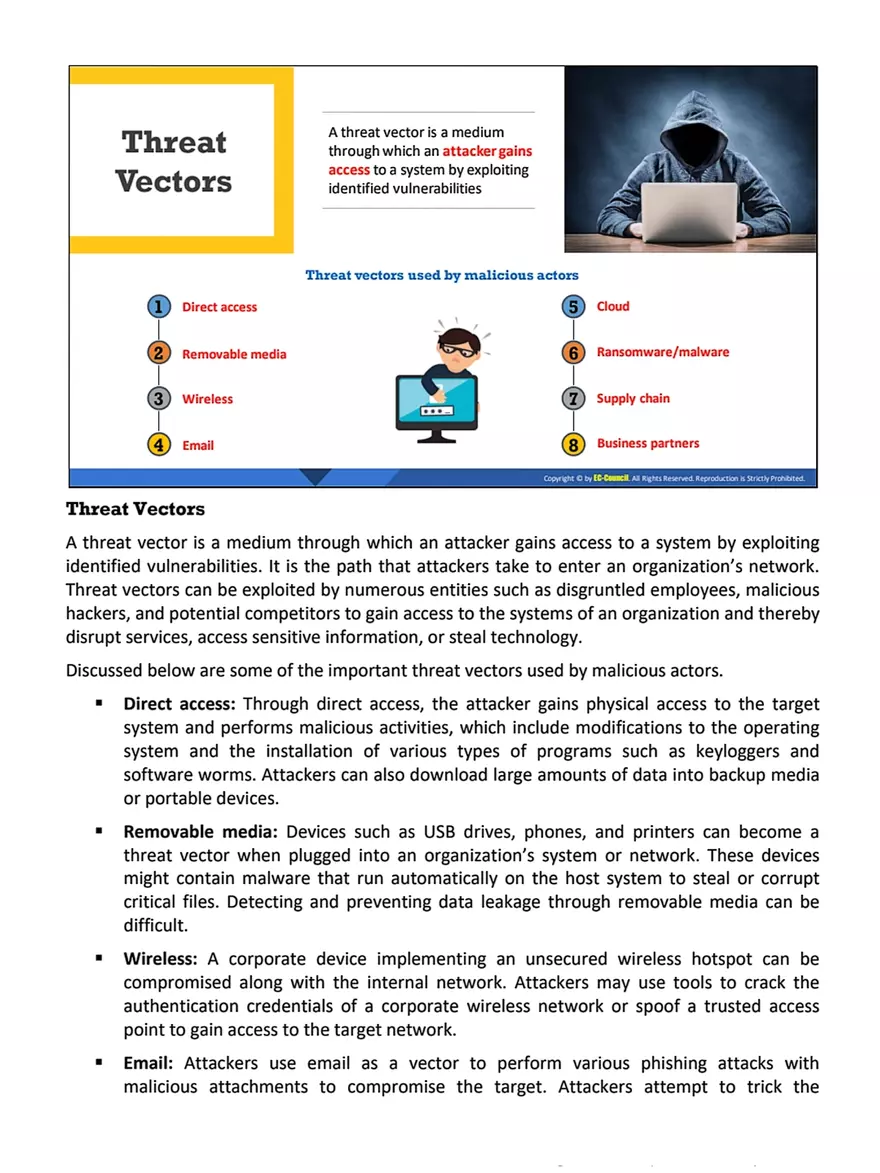
Threat Vectors
-
University:
Campbell University -
Course:
HSEC 444 | Cybersecurity Academic year:
2021
-
Views:
81
Pages:
2
Author:
sonalhava9qv
Related Documents
- Advancements in Natural Language Processing
- How is the Complexity of an Algorithm Affected When it Encounters
- How Binary Search Algorithm Works and Time Complexity
- Variables Robotc
- CSS Styling
- LaTeX Command Summary Vocabulary
- Introduction and Computational Thinking Pt 1
- Tuning MATLAB For Better Perfomance
- Python for Non-programmers - A Gentle Introduction
- Techniques for Practical ORAM and ORAM in Hardware
- Shortest Paths Bellman-Ford Algorithm
- Data Stream Algorithmics
- Systems I — Lab 6 Conditional Statements and Loops in Assembly
- Clock Filter Algorithm
- COSC-311 Sample Midterm Questions
- What is the Travelling Salesman Problem
- Hash Functions and How They Contribute to Hash
- NTP in the Internet
- NTP Daemon Architecture
- Computer Network Time Synchronization
Report
Tell us what’s wrong with it:
Thanks, got it!
We will moderate it soon!
Report
Tell us what’s wrong with it:
Free up your schedule!
Our EduBirdie Experts Are Here for You 24/7! Just fill out a form and let us know how we can assist you.
Take 5 seconds to unlock
Enter your email below and get instant access to your document