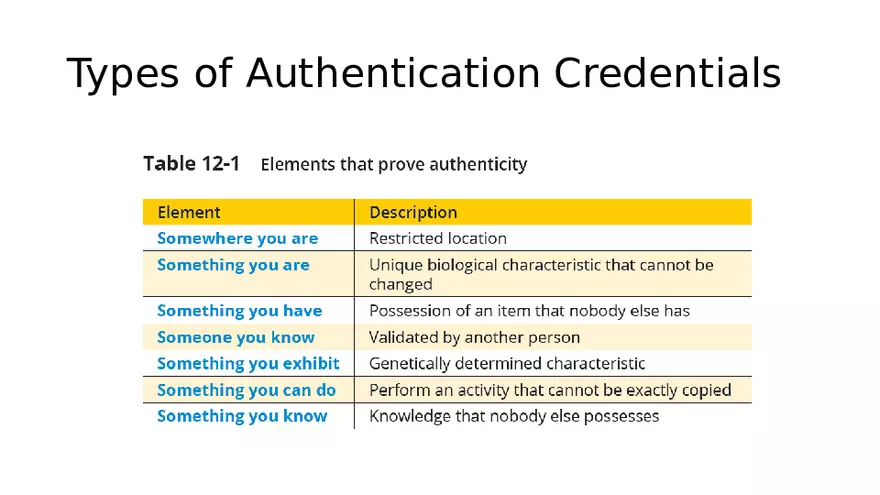
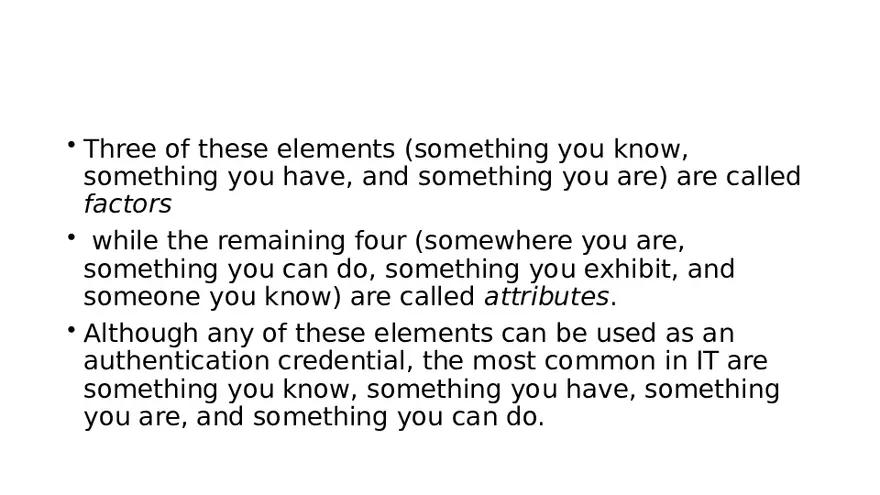
Lecture Note
Authentication in Information Security Part 1
-
University:
Campbell University -
Course:
HSEC 444 | Cybersecurity Academic year:
2023
-
Views:
315
Pages:
10
Author:
ilikemyicons0y5
Related Documents
- Quiz Computer Science Graph Optimization Algorithm
- Storytelling With Data
- Quiz 6: Defying The Data Threat
- Quiz 4: Countering Digital Criminal Attacks
- Quiz: Applying CSS Styles to Web Pages
- Quiz Computer Science Quantum Algorithms In Data Security
- Quiz Computer Science Implementation Of Bank Operation Simulation
- Quiz Computer Science Steady-State Model Simulation
- Quiz Computer Science Artificial Intelligence System Simulation
- Quiz 1: Cryptographic Security And Risk Management
- Quiz 3: Security In Electronic Content Validation
- Quiz Computer Science Html Tags In Data Selection
- Data Analytics Practice Exam 8
- Dimensional Framework (Qualitative vs Quantitative)
- Dimensional Framework (Attitudinal vs Behavioral)
- Data Manipulation Techniques: It Specialist Practice Exam
- Quiz Computer Science Chatbot Technology In Service Improvement
- Type of Chart Data Visualization
- Quiz 5: Data Visualization - Real-World Applications
- Quiz 8 : Fundamental Of Data Visualization – Effectiveness Of Chart Usage
Report
Tell us what’s wrong with it:
Thanks, got it!
We will moderate it soon!
Report
Tell us what’s wrong with it:
Free up your schedule!
Our EduBirdie Experts Are Here for You 24/7! Just fill out a form and let us know how we can assist you.
Take 5 seconds to unlock
Enter your email below and get instant access to your document